How many emails do you find yourself sending or receiving in a typical day? Whether it’s an important message from your manager or a notification from your favorite social media platform, email has woven itself into the very fabric of our modern lives, both personally and professionally.
While emails have undoubtedly revolutionized the way we communicate, they also bring along a set of digital dangers. In today’s digital landscape, the convenience of emails comes hand in hand with the increased risk of spam and phishing attacks.
In fact, did you know that in July 2021, 283 out of 336 billion emails sent were spam? Also, around 3.5 billion phishing emails are sent daily? You can check your own inbox and find out!
Spam emails clutter your inboxes, while phishing emails will trick you into revealing sensitive information, posing a risk of data security. These emails are annoying, sneaky, malicious and dangerous. You should avoid them at any cost!
Fortunately, there are steps you can take to identify these emails, and protect yourself from their threats.
In this article, we will explore the practical strategies to spot and avoid falling victim to spam and phishing emails. Let’s start with their introduction:
Spam
Spam, also known as junk email, is any unsolicited digital communication sent in bulk. While it is typically sent via email, it can also be sent through text messages or social media.
Phishing
Phishing is an attack used to steal user data such as login credentials and credit card numbers.
Phishing emails are fake emails that look like they are from legitimate sources (such as your bank, or your credit card company). The goal of phishing is to steal your personal information, or to trick you into clicking on a malicious link. When the recipient clicks this malicious link, it can lead to installing malware, freezing your computer, or a ransomware attack.
Phishing emails can be very convincing. They may have the company’s logo and official branding, and they may use your name and other personal information.
Phishing Scam Tactics
Phishing scam tactics are deceptive and manipulative strategies used by cybercriminals to trick individuals into revealing sensitive information, such as passwords, credit card details, or personal information. Here are common phishing scam tactics:
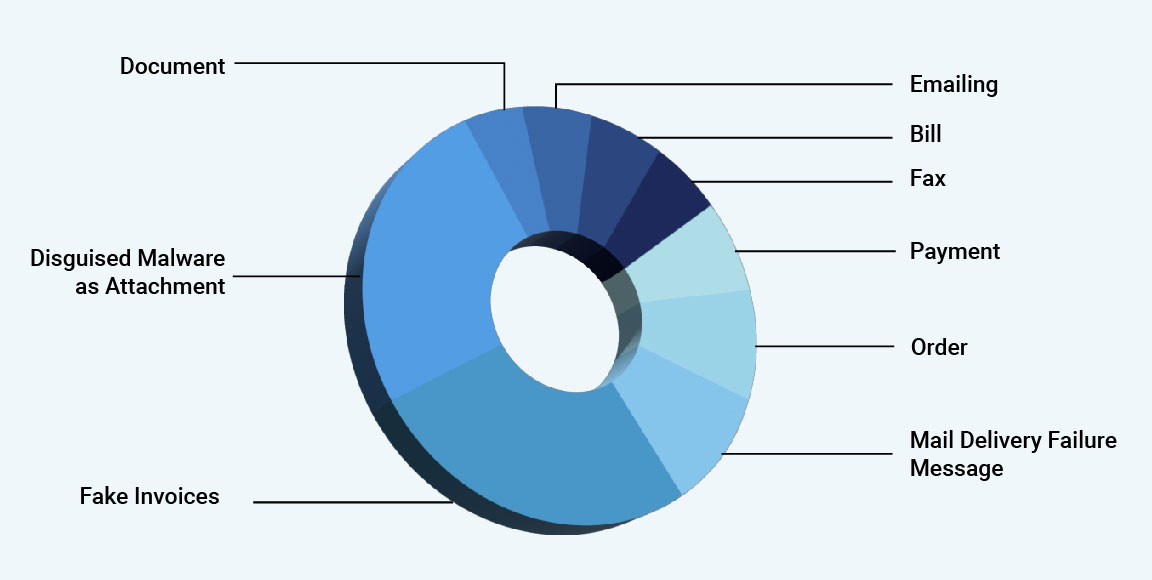
Understanding these phishing scam tactics is crucial for individuals and organizations to stay vigilant and adopt effective measures to protect themselves against phishing attacks.
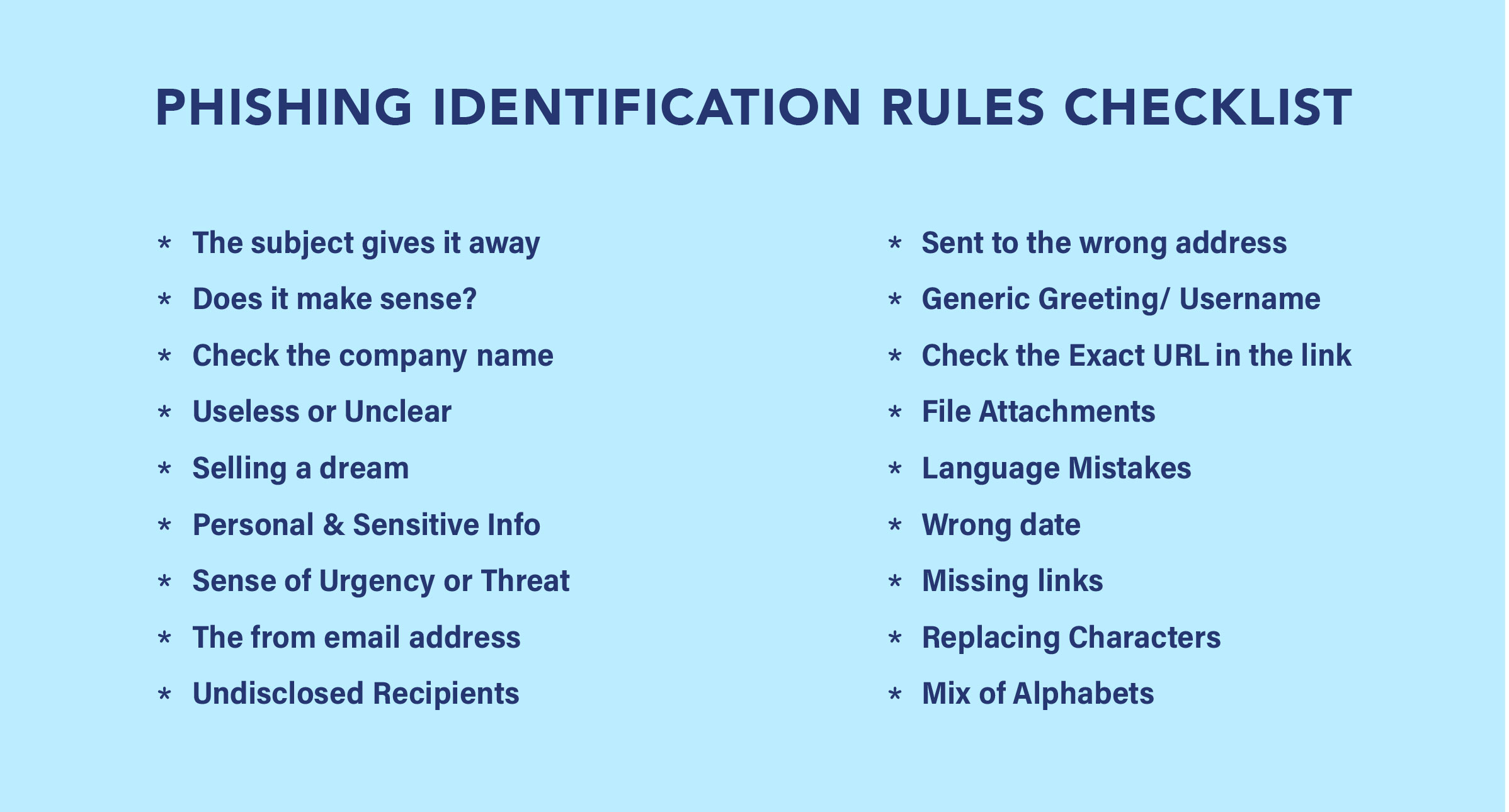
7 Signs of Phishing Email :
It is easy to fall into the trap of phishing emails as the senders try to make it as believable as possible. However, there are some key signs you can watch out for that might be indicative of it being a phishing email.
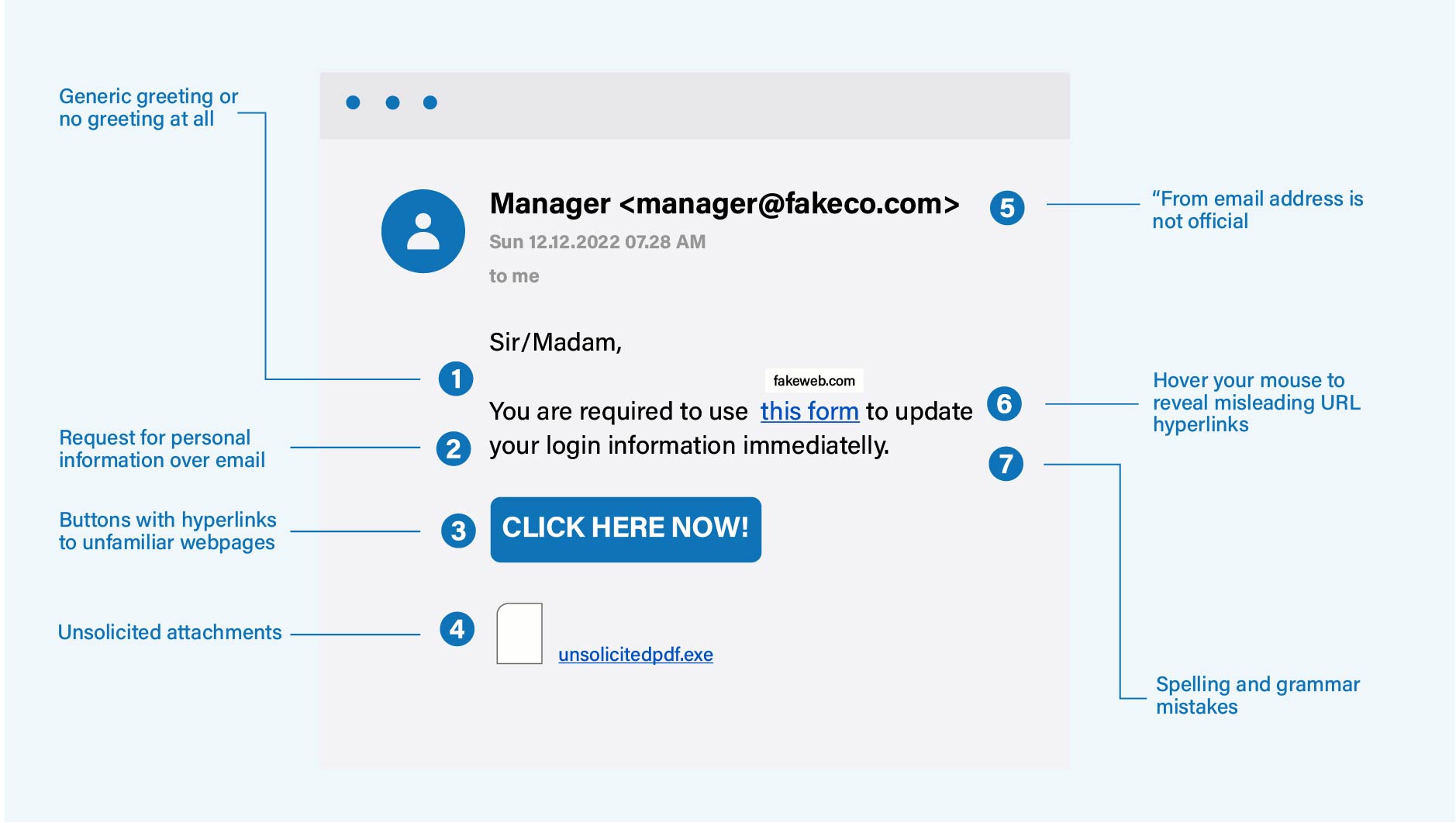
Recognizing these signs helps individuals identify potential phishing attempts and take appropriate precautions to avoid falling victim to scams. Always exercise caution and verify email legitimacy before taking any action.
Phishing Emails Types
These emails do not always come in pre-defined formats. Scammers use a lot of different types of emails to deceive you.
Some of the most common phishing scam email types are explained below
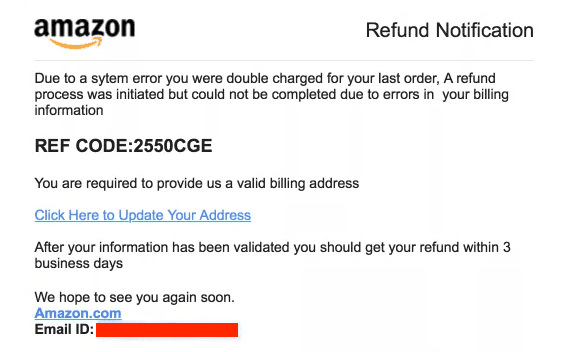
Deceptive Phishing:
Deceptive phishing is a sophisticated form of cyber attack where cybercriminals impersonate trusted entities or organizations to manipulate individuals into revealing sensitive information. It includes impersonation, baiting, fear or urgency tactics, mimicking official communications, malicious links or attachments, data harvesting, and avoidance of detection techniques.
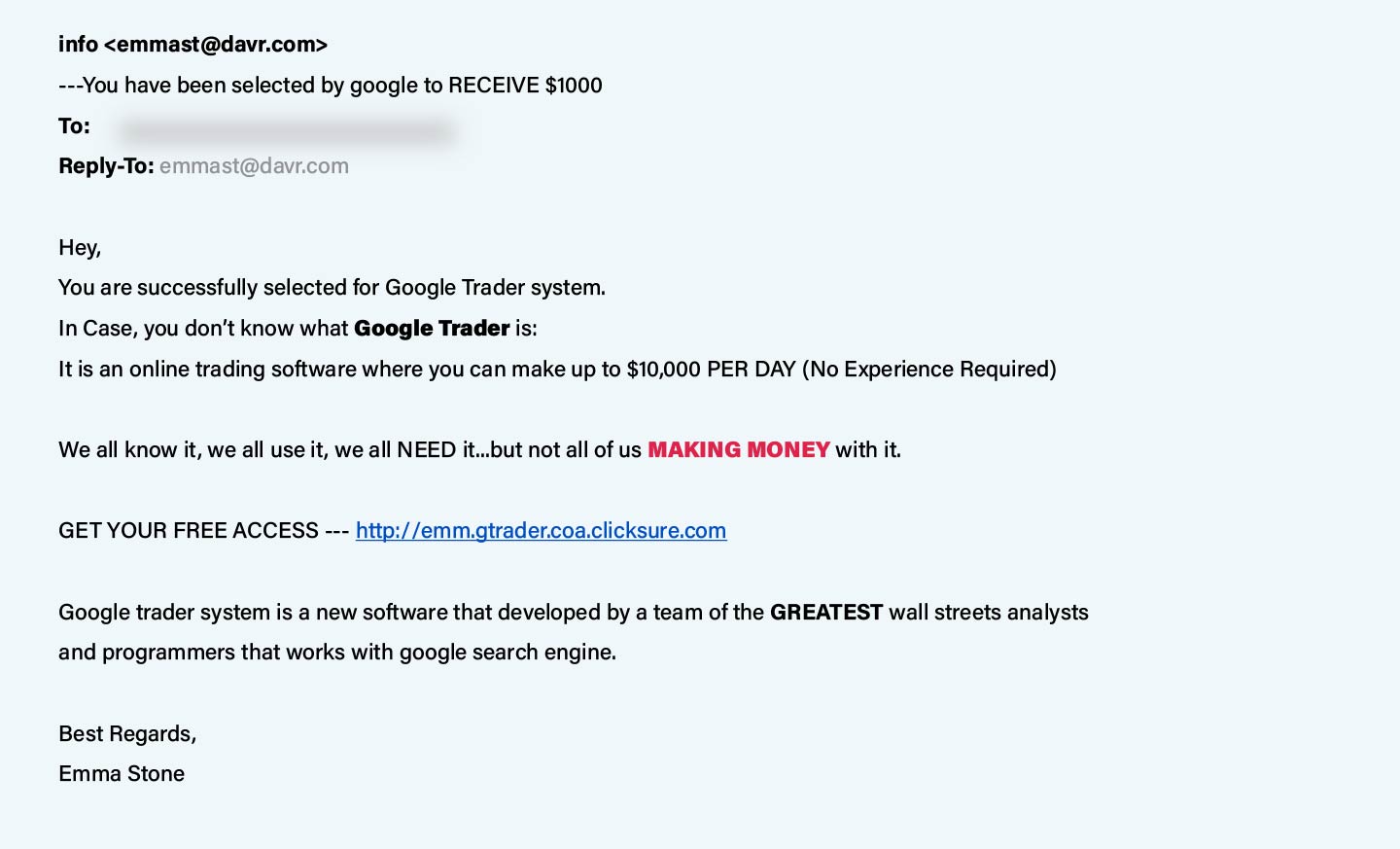
Reveal Money-Making Secret:
“Reveal Money-Making Secret” phishing is a deceptive tactic used by cybercriminals to lure individuals into believing they can uncover secret ways to make money quickly or easily. It includes False promises, Urgency and FOMO(Fear of Missing Out), misleading claims, requests for personal information or payment, malicious links or downloads, masking authenticity, and exploitation of greed. e.g.
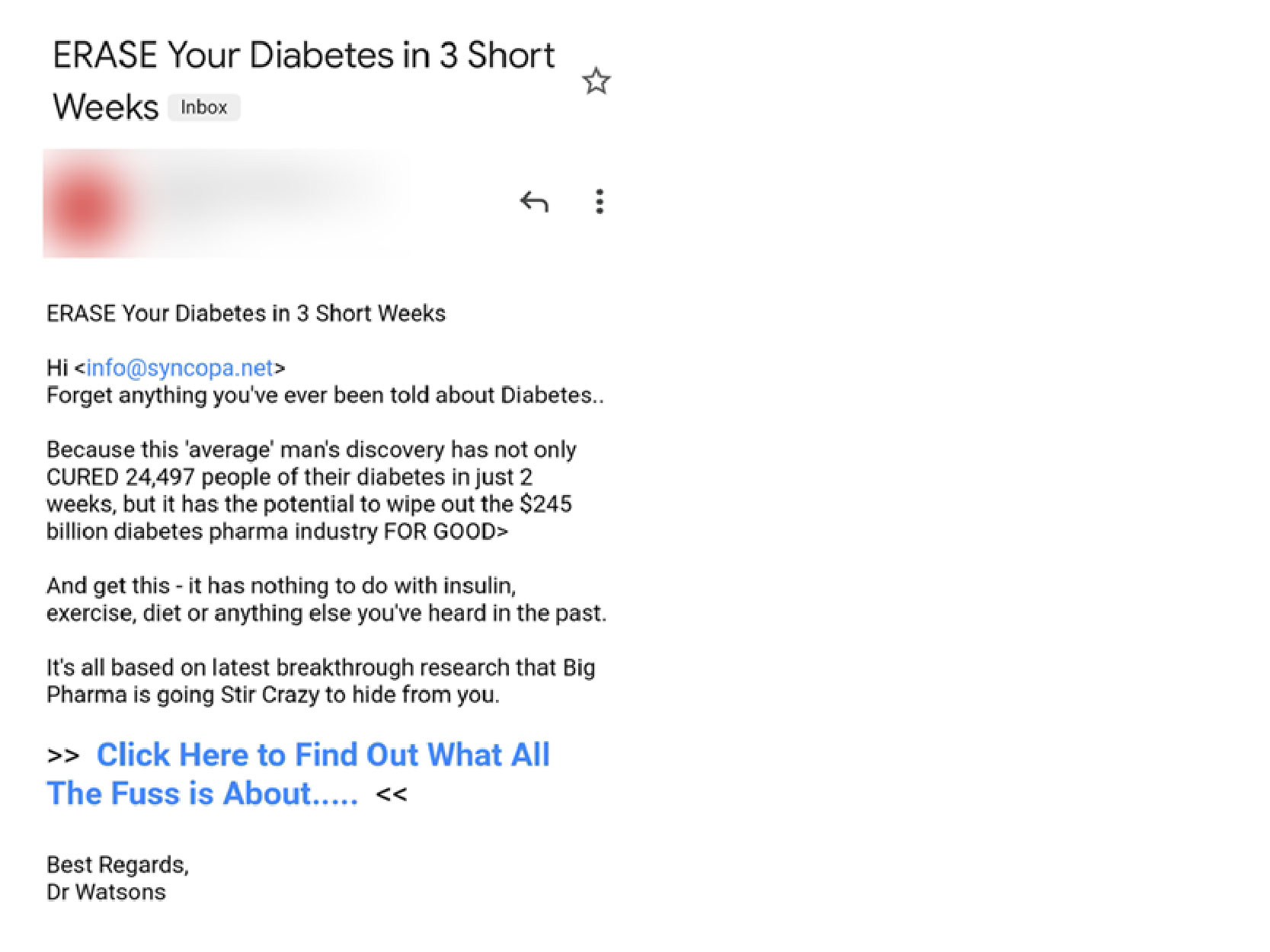
Offer a Cure:
“Offer a Cure” phishing is a tactic where cybercriminals claim to have a cure, solution, or remedy for a specific problem or concern. These emails exploit individuals’ vulnerabilities, fears, or desires for health, financial stability, or personal issues. e.g.
Money Offered:
“Money Offered” phishing is a type of scam where cybercriminals bait individuals with the promise of easy money. They typically pose as organizations, wealthy individuals, or lottery systems claiming that the recipient has won a prize, is eligible for a grant, or can earn significant sums quickly. e.g.
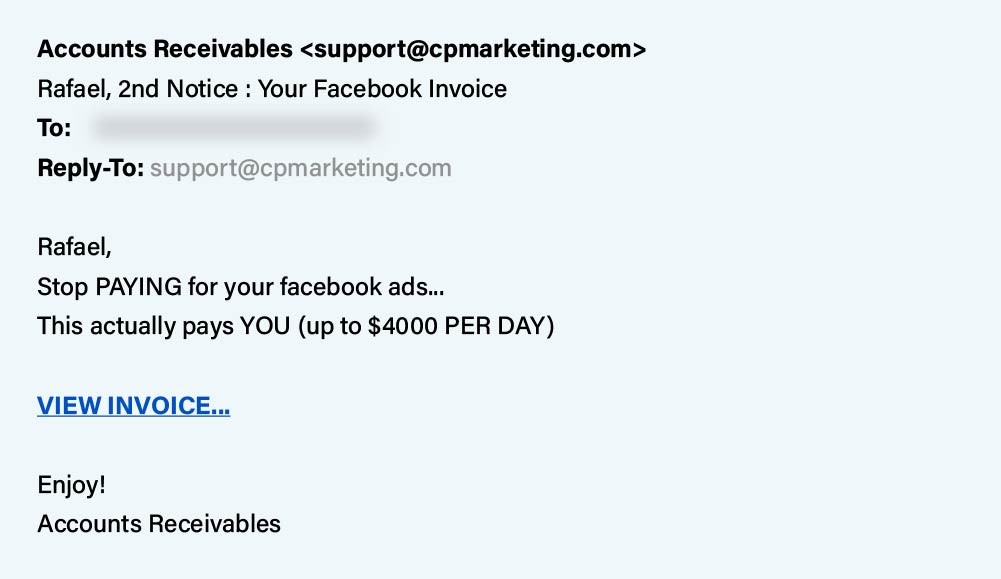
Money Requested:
“Money Requested” phishing involves cybercriminals impersonating trusted entities, such as friends, family, or organizations, to request funds from individuals. The scam plays on empathy, urgency, or the desire to help, ultimately coaxing victims into sending money.
Phishing Attack Prevention:
As they say, prevention is better than cure. You can prevent those attacks from happening with a better security plan for yourself. Here are some of the tactics you can use:
- Enforce strict password management policies and should be required to frequently change their passwords and not be allowed to reuse a password for multiple applications.
- Implement Two-factor authentication. It is a security process that requires users to provide two different authentication factors to verify their identity.
- For enterprises, a number of steps can be taken to mitigate using DNS server records, email gateway servers, and many more.
- Implement robust email filtering systems that can detect and block known phishing email signatures, domains, and malicious attachments. This helps in reducing the number of phishing emails reaching users’ inboxes.
- Educational campaigns can also help diminish the threat of phishing attacks by enforcing secure practices, such as not clicking on external email links or, the latest phishing and spam tactics and tools, inspecting attachments carefully, and hovering over links before clicking.
- Utilize anti-phishing software or tools that can detect and block phishing attempts by analyzing patterns, behaviors, and known phishing indicators.
- Train employees to be cautious about the information they share on social media, as attackers often use social engineering techniques to gather details for phishing attacks.
- Create a culture where employees feel comfortable reporting suspicious emails or incidents promptly. Establish clear reporting procedures and channels.
- Implement a robust backup and recovery strategy to ensure that critical data is regularly backed up and can be restored in case of a successful phishing attack or other cybersecurity incidents.
Conclusion :
In conclusion, protecting yourself from phishing and spamming threats requires being careful and well-informed. It’s crucial to be cautious when you get messages that seem urgent or ask for personal or financial details out of the blue.
Learning about the latest tricks that scammers use is important. You can also stay safe by using extra security measures like two-step verification, keeping your devices up to date, and having strong email filters. Checking who sends you emails and reporting anything that looks fishy adds more safety. Just remember, being aware and taking action helps keep you and others safe online.
We have explored some warning signs that can help you navigate these treacherous waters. By staying vigilant, questioning the unexpected, and safeguarding your personal information, you can shield yourself from cybercriminals.
Remember, your online safety is in your hands, so stay safe and help others stay safe by educating them.
.………………..
Gurzu is a full-cycle Software development company. Since 2014, we have built software for many startups and enterprises from all around the world using Agile methodology. Our team of experienced developers, designers, and test automation engineers can help to develop your next product.
Read more about our services here.
Have a tech idea you want to turn into reality? Book a free consulting call.

